Our approach. It all starts with a master plan
- Evaluate maturity of existing cybersecurity management system
- Quantify major cybersecurity risks and bind them to business risks
- Define target enterprise security architecture
- Build cybersecurity project portfolio
- Produce 3-year cybersecurity development master plan to support business goals
Focus on cybersecurity risk management
▪ Define detailed cybersecurity risk management process, including risk assessment
▪ Align cybersecurity risk management with enterprise risk management
▪ Identify risk scenarios which concern business stakeholders the most
▪ Assess completeness and maturity of existing cybersecurity control framework
▪ Quantify risk scenarios
▪ Build cybersecurity risk map aligned with business risks
▪ Produce risk treatment plan and accept residual risks to give a priority to what worth it
▪ Define KRIs for proper risk monitoring
▪ Identify requirements for sGRC / ITRM system
Focus on application security
▪ Define a solid application security program to cover whole application lifecycle
from business requirements to post-production maintenance and support
▪ Integrate security requirements management and architecture review practices
▪ Design hardened CI/CD pipeline with integrated security tools
▪ Gain visibility and implement protection for container management
▪ Define a detailed findings triage process to ensure priority is given where it needs to
▪ Get legacy applications onboard into secure lifecycle
▪ Assess security of web and mobile applications (including code review)
▪ Ensure security awareness for development teams
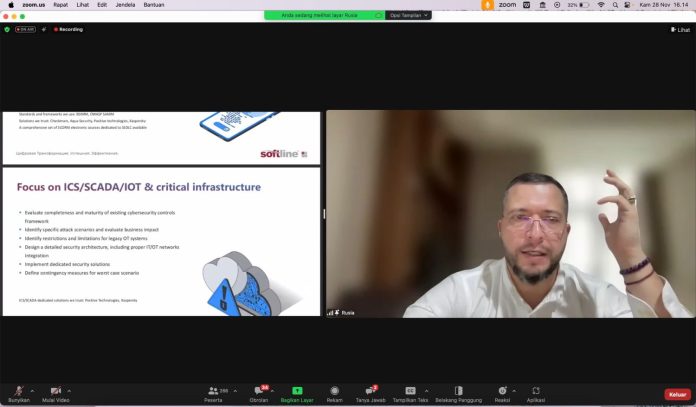
Focus on ICS/SCADA/IOT & critical infrastructure
▪ Evaluate completeness and maturity of existing cybersecurity controls
framework
▪ Identify specific attack scenarios and evaluate business impact
▪ Identify restrictions and limitations for legacy OT systems
▪ Design a detailed security architecture, including proper IT/OT networks
integration
▪ Implement dedicated security solutions
▪ Define contingency measures for worst case scenario
Focus on awareness among employees
E-courses, memos, posters, newsletters, videos, screensavers and others
➔ Development of educational materials on any topic related to information
security for various user groups.
➔ Creation of training materials for specialized areas in information security and
information technology, including administration of information security tools.
➔ Writing cybersecurity guidelines.
➔ Conducting anonymous surveys to assess the real situation regarding compliance with
information security rules in the organization.
➔ Layout of posters on data protection themes, considering corporate design specifics and
Customer’s design preferences.
➔ Creating videos on information security featuring developed characters and in
accordance with the Customer’s brand guidelines.
➔ Preparation of articles/reviews on cybersecurity on behalf of the Customer’s
information security unit (possibly on a monthly basis).
➔ Design of screen savers considering the specifics of tasks and the
Customer’s corporate style.
➔ Construction of simulators and educational games tailored to the Client’s tasks.
Focus on so-called cyber-polygon
DevSecOps
- DevSecOps basics
- Instruments (programming language)
- Communications
- Code Integration
- Team interaction
- Agile development
Cybersecurity
- How to attack incl through
vulnerabilities exploitation
- How to build secure infrastructure
- Threat hunting and vulnerability
management
- Investigation
- Risks minimization
Infrastructure
- Disaster recovery plan
- Business continuity
- Best solutions to defense
- Implementation
- Recovery
- Communication IT+IS
Business
- Business modeling
- Communications
- Finance vs Security
- Roadmap – how to build
- Efficiency of expenses
- PR